Understanding Campus Firewalls
What is a firewall?
Firewalls are network devices that detect and prevent unwanted or malicious traffic from reaching your computer or server while allowing you to use the network as normal. Firewalls on the UNC network are maintained by ITS.
Firewalls help secure your computer
UNC’s firewalls are positioned between the computers and servers they protect and other networks, including other on-campus networks and the Internet. These firewalls run custom operating systems and use advanced security features to provide protected computers and devices with multi-layered protection against malware and other attacks.
The University provides these firewalls at no cost to clients in order to increase the security of sensitive or mission critical information and services.
While the campus firewalls stop many attacks from reaching your computer, it is still important your computer have its own protections and updates enabled. For questions about how to protect your desktop computer, or to verify it is as secure as it should be, contact your local IT support or the ITS Service Desk at 919-962-HELP.
Hardware firewall service for University departments or groups
University departments, research centers, and other administrative units need to protect a diverse array of resources, including users and servers of varying types and functions. On-campus hardware/network firewalls are an important component of that and are available to any on-campus department, unit, research center, or group.
Devices and networks protected by the firewalls are organized into one or more “zones” made up of different types of systems with similar levels of risk. Zones can be categorized as one of three general types: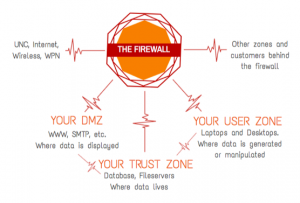
- User Zone: protects user workstations and other user-related devices such as printers. The user zone is often where sensitive information is developed.
- DMZ: protects high-risk servers that serve a public purpose, such as web servers or those used for collaborative research. The DMZ is where sensitive information is
- Trust: servers that store data with restricted access, such as a database only accessible to a specific set of developers or a file server accessible only by one department or one team within a department. The trust zone is where sensitive information is stored at rest.
Departmental firewall service is available to any on-campus department, unit, research center, or group.
The best way to determine the appropriate way to implement hardware/network firewalls is to consult with the ITS Information Security Office regarding the resources you wish to protect.
This document draws on the structure and content of McDowell, M. & Householder, A. (2004). Understanding Firewalls. Carnegie Mellon University. Made available by the United States Computer Emergency Readiness Team (US-CERT).