October marks National Cybersecurity Awareness Month. This page was created as a handout to introduce the Security Operations and Incident Response (SecOps & IR) pillars within the UNC Information Security Office.
What is SecOps & IR at UNC?
The goals of the SecOps & IR Team are to:
- Prepare the UNC environment to withstand cybersecurity threats: stop incidents before they occur.
- Identify cybersecurity incidents when they do occur and rapidly contain them to minimize damage.
- Eradicate threats from the environment and recover normal operations after an incident.
- This requires a full investigation, understanding the risks that led to the incident, to ensure operations are brought back in a way that is resilient and not vulnerable to the same threat.
- Follow established Digital Forensics and Incident Response (DFIR) practices to ensure evidence is preserved in case it is needed for legal proceedings.
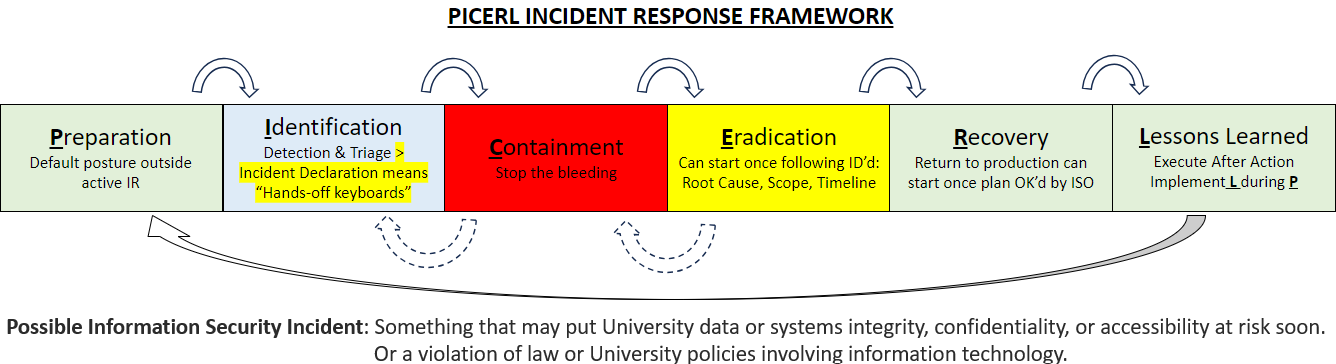
The UNC SecOps & IR Team uses the PICERL Incident Response Framework from the SANS Incident Handler’s Handbook
What does a typical day look like for a SecOps & IR team member?
In practice, the majority of SecOps analysts’ efforts are spent in the Preparation & Identification phases. This includes tasks such as:
- Creating, tuning and triaging alerts from our Security Information and Event Management (SIEM) solution. This system is vital in collating and summarizing information from hundreds of applications and endpoints across the network. The team responds to multiple alerts daily which generate leads on “Possible Information Security Incidents” that must be investigated. For example, if Antivirus detected malware on a host, are there other indicators to suggest the malware deployment was successful (e.g., impossible travel logons or suspicious “lateral movement” activity).
- Responding to reports and investigating leads of “Possible Information Security Incidents” from UNC stakeholders. We never know when or where a threat may successfully exploit a vulnerability to create an incident: as described in the Information Security Incident Management Standard we are available 24x7x365 through 919-962-HELP or help.unc.edu (critical incident) to respond to Possible Information Security Incidents that risk exposure of UNC Sensitive Information or significant events that jeopardize mission critical infrastructure or large sets of users on the network, e.g., ransomware.
- Maintaining and monitoring the Endpoint Detection and Response (EDR), Vulnerability Management Detection and Response (VMDR) and other SecOps tooling.
- Monitoring and researching known vulnerabilities as well as testing and uncovering vulnerabilities in the UNC network.
- Engaging with UNC stakeholders to promote cybersecurity training and awareness. This can include sharing active threats observed via our safecomputing site, assisting units with deploying phishing simulation exercises, and working with service owners and data teams to incorporate security operations into their systems and processes.
Once a “Possible” incident has been triaged and declared as a likely/confirmed incident, the SecOps team begins Containment. Our focus is to quickly identify the root cause (e.g., was a system/software vulnerability leveraged), the scope (e.g., were other systems, users or sensitive information targeted) and the timeline of events (e.g., when was the first observation of the vulnerability being exploited, both in our network and publicly sources). Once these facts are known, we can begin the Eradication and Recovery phases to ensure that systems and services are brought back in a resilient manner. Significant Incidents where sensitive information or mission critical services are impacted will always involve a formal After Action review overseen by the UNC Chief Information Security Officer (CISO) to ensure the incident is understood and the organization is equipped to incorporate Lesson Learned to reduce the likelihood of recurrence.
Where should I start if I’m interested in a career in Cyber?
Cybersecurity careers are rewarding and in demand. Pursuing a career in cybersecurity means that you’ll be committing yourself to lifelong learning. Hack the box and Tryhackme are great resources for hands-on exposure to the tools of the trade. Joining a professional network such as ISC2 is also a way to explore the field and find career outreach and mentorship.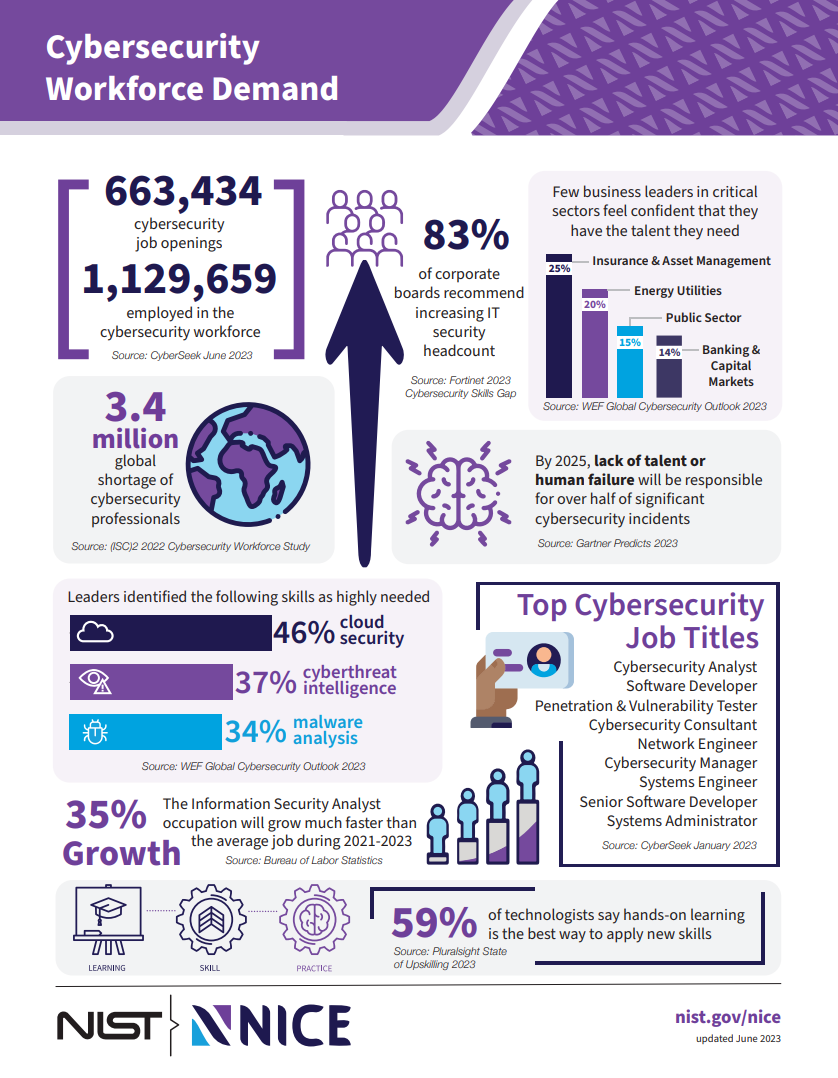
What should I know about SecOps & IR?
As the saying goes: a chain is only as strong as the weakest link. Everyone has an important and shared responsibility to maintain security at UNC.
Here are some things you can do to support and improve SecOps & IR:
- Keep up with the Information Security Awareness Training. The UNC Security Policy and Standard requires annual security awareness training but this is always available for reference if you want a refresher. The training summarizes important topics such as recognizing phishing and keeping software up-to-date.
- Remember: If people use a personal device for University business, the owner of the personal device must make sure the personal device meets the same security standards as University-owned devices. This is especially relevant for student employees or research involving Tier 2 (Confidential) or Tier 3 (Restricted) sensitive information. Keeping your personal device, and information, separate from UNC Sensitive Information (i.e., data, other than your own personal information, that UNC has a legal or contractual obligation to protect, including assuring IR investigations and reporting) can help avoid privacy issues and limit the likelihood of data leakage.
- Get to know your IT Support Resources. Anyone can contact 962-HELP or help.unc.edu to request assistance or report issues related to UNC IT and Information Security. We’re here to help!
- Maintain good password hygiene as described in the UNC Password Standard.
- Sign-up for Carolina Key (i.e., passwordless logon). This is supported on many of the sites and services where you logon with your Onyen and allows you to use more modern authentication.
- Use a Password Manager. Although these services have suffered their share of incidents, use of a password manager is still the best way to create strong, unique passwords for sites and services to ensure a breach at one does not extend to password spray/reuse attacks. Make sure that your master password is strong and memorable!
- Use Multifactor Authentication (MFA). Where feasible, choose mobile app-based MFA (e.g., Microsoft Authenticator, Google Authenticator) instead of SMS to reduce the risk of SIM swapping.

https://imgs.xkcd.com/comics/password_strength.png
What should I do if I suspect a Possible Information Security Incident
UNC maintains the Information Security Incident Management Standard which describes what to do if you suspect a Possible Information Security Incident, defined as “Something that may put University data or systems integrity, confidentiality, or accessibility at risk soon. Or a violation of law or University policies involving information technology.” See the Standard for some common examples of concerns that must be reported.
The following are some important takeaways:
- “If you believe that someone’s life may be in danger, call 911 at once!”
- “If you have found a Phishing message but have not interacted with it in a way that might compromise your account, you can report the message” using the Report button in Outlook / heelmail.
- For any other Possible Information Security Incident, contact the Service Desk by phone (919-962-4357/HELP) and ask for a critical incident to be created and sent to the Information Security Office (or School of Medicine Information Security Office if the incident specifically involves SOM personnel or assets). Supply a contact number and be available at that number. Expect a call within an hour.
- While waiting for the call from the incident handler, try not to do anything that will change the device or any evidence you might have about the concern (i.e., “hands off keyboard,” do not run antivirus scans, shutdown the computer, etc.).