Key Takeaways:
- UNC is rolling out Phishing-Resistant MFA through the CarolinaKey initiative. Setting up CarolinaKey will increase your security posture and reduce the number of times you have to type a password + approve an MFA push.
- You are 99% less likely to get hacked if your account uses MFA. Enable MFA wherever it is available, especially your personal email and financial services.
- Any MFA is better than no MFA however the latest Phishing-Resistant MFA option addresses weaknesses present in other options.
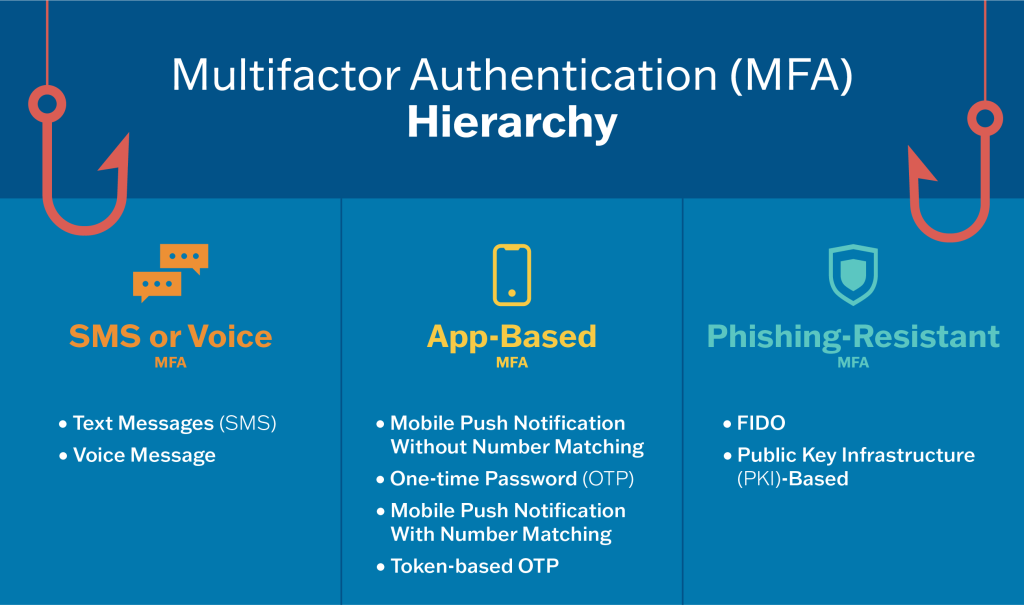
CISA MFA Hierarchy accessed from https://www.cisa.gov/MFA - Use the strongest available MFA supported by your service provider. If Phishing-Resistant MFA isn’t supported by the service provider, App-Based with Number Match or One-time Password are preferred over SMS/Voice options.
- Be aware of the cyber threats to MFA:
- Never approve an MFA notification that you did not initiate. Decline it and reset your password.
- If you receive an unsolicited call or text to click a link or enter MFA codes/approvals, report it as SPAM.
- Always report a lost or stolen device with access to UNC systems to 919-962-4357(HELP) / help.unc.edu. Ask for a critical incident to be created if you believe UNC Sensitive Information may be at risk.
- If the lost/stolen device is enrolled in CarolinaKey, delete it.
CYBER THREATS TO MFA
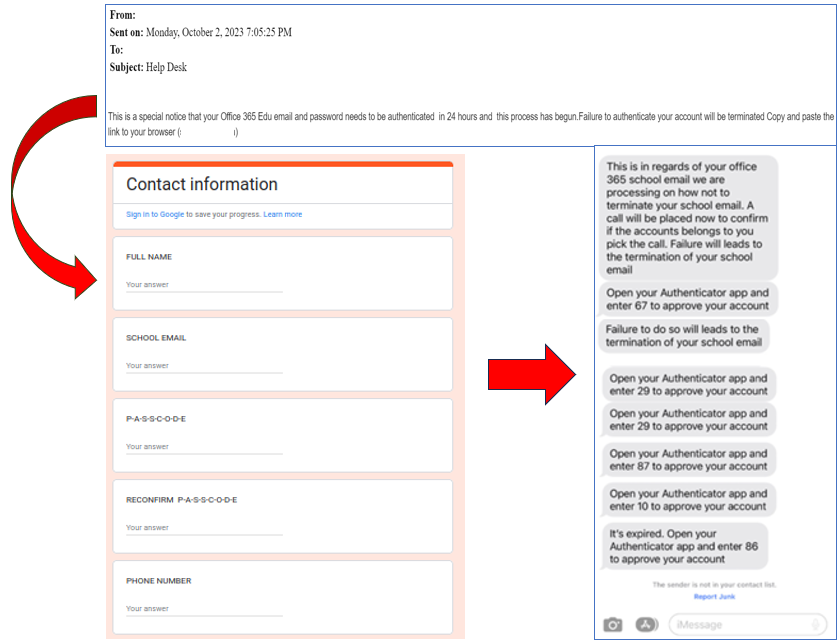
Cyber threat actors have used multiple methods to gain access to MFA credentials. Phishing is one of the most prominent methods used by threat actors since it is both low cost and effective. In a recent phishing campaign, a threat actor used various scams (e.g., account termination, job placement opportunity, etc.) to trick us into providing email, phone number and password into a Google docs form. Once this information was obtained the threat actor used the “push bombing” method to get around SMS and App-Based MFA, including with Number Match.
Be wary of scams and never accept an MFA notification you did not initiate.
The goal of Phish-Resistant MFA is to reduce the risk of account takeover in the event the threat actor manages to gain passwords and MFA codes such as in the aforementioned scenario while also supporting more convenient “password-less” authentication methods such as fingerprint, face recognition, PIN (combined with a “Trusted Platform Module” crytoprocessor found in most computers after 2016), and hardware security keys such (e.g., Yubikey or FIDO). Significantly, the sensitive authentication data, private key, involved with these methods remains securely stored on your device; therefore, this form of MFA is “resistant” to phishing methods that use fake logon forms or similar methods that attempt to “trick” you into providing the information necessary for the threat actor to logon to the account.
Phish-Resistant MFA does not eliminate all risks from phishing: one must still be vigilant to avoid suspicious email attachments or links that potentially lead to malware that could expose your device, for instance.
| Threat | Description | Phish-Resistant MFA | App-Based w/ OTP or Number Match | App-Based w/o Number Match | SMS or Voice |
| Stolen Device | file a police report and notify the service provider to revoke MFA registration | Vulnerable | Vulnerable | Vulnerable | Vulnerable |
| Phishing | a form of social engineering in which cyber threat actors use email or malicious websites to solicit information | Resistant | Vulnerable | Vulnerable | Vulnerable |
| Push bombing | also known as push fatigue; the threat actor bombards you with MFA notifications until you “Accept” | Not Applicable | Resistant | Vulnerable | Vulnerable |
| SS7 protocol vulnerabilities | threat actors exploit SS7 protocol vulnerabilities in communications infrastructure to obtain MFA codes sent via text message (SMS) or voice to a phone | Not Applicable | Not Applicable | Not Applicable | Vulnerable |
| SIM Swap | a form of social engineering in which cyber threat actors convince cellular carriers to transfer control of your phone number to a threat actor-controlled SIM card, which allows the threat actor to gain control over your phone. | Not Applicable | Not Applicable | Not Applicable | Vulnerable |
Adapted from CISA’s Implementing Phishing-Resistant MFA